The SMART VALOR team is making every effort to ensure the security of our platform. Through our Bug Bounty Program we invite security researchers, individuals or groups, to responsibly assess the security of our platform and report their findings back to us. We wholeheartedly welcome all vulnerability reports on the SMART VALOR domains but will reward only the first disclosure of critical or high severity vulnerabilities. #### Any security assessment or other types of testing activity performed against SMART VALOR domains outside this program is strictly forbidden!
Please note that participation in this program is voluntary and based on “bona fide“. This implies that the security researchers participating in this program: - read, understand and fully comply with the program requirements described here - follow a responsible assessment and disclosure model - will NOT, under any circumstances, attempt to exploit the discovered vulnerabilities (e.g. cause disruption to a service, access/tamper/leak confidential information) - understand that SMART VALOR will re-evaluate the severity of reported findings during the internal validation process - understand that SMART VALOR has no obligation to prove the initial disclosure of a finding to any subsequent reporters - allow SMART VALOR equitable time to evaluate and remediate the findings - can disclose their findings to 3rd parties only with written consent from SMART VALOR - understand that SMART VALOR will solely decide which reports are awarded and the award amount If the Security Researcher demonstrates inappropriate behaviour / language during his participation in this program, he/she will be immediately disqualified from the program.
#### We urge anyone accessing our platform, for any kind of purpose, to report the encountered security issues without attempting to exploit them! SMART VALOR takes legal action against exploitation attempts.
### Testing Requirements - Testing approach is “black-box“. The design/infrastructure/implementation of the platform is not known by the tester. - Testing will be performed on your own accounts only. Any kind of test on other accounts is strictly forbidden. - Testing using social engineering techniques is not recommended. - DDoS and resource exhaustion attacks are strictly forbidden. DoS attacks that are triggered by exploiting the platform’s business logic are allowed. - Automated tests / vulnerability scans are only allowed with prior explicit permission from SMART VALOR. - Security of hardware, offices and/or employees of SMART VALOR is outside the scope of the program. ### Information Handling Requirements Participating in this program is conditioned by the obligation to strictly follow the below information handling requirements. - Do NOT access personal information, leak/manipulate/tamper user data or cause disruption of service. - Do NOT disclose any findings to the public, or to any 3rd party unless SMART VALOR grants you explicit permission. - Do NOT submit your report or request information related to it on any communication channel except the one indicated in the “Guidelines for Report Submission” (e.g. Telegram messages, Facebook posts are strictly forbidden). If you do not get any feedback within 5 working days, please resubmit your report and include all your questions.
### Guidelines for Report Submission - Submit your findings report only to security@smartvalor.com . Other communication channels are not accepted. - Provide your name and contact information along with your submission. - Your report should contain the vulnerability description, detailed steps to reproduce it (including associated screen shots / video) and remediation description. ### Eligibility Requirements for Monetary Awards - Your activity should abide by the testing requirements, information handling requirements and report submission guidelines. - You must be the first researcher to report the vulnerability. - The vulnerability must address a “bona fide” security problem (some examples provided at the end of this page). - You cannot be a current or former employee of SMART VALOR or our contractors/data processors.
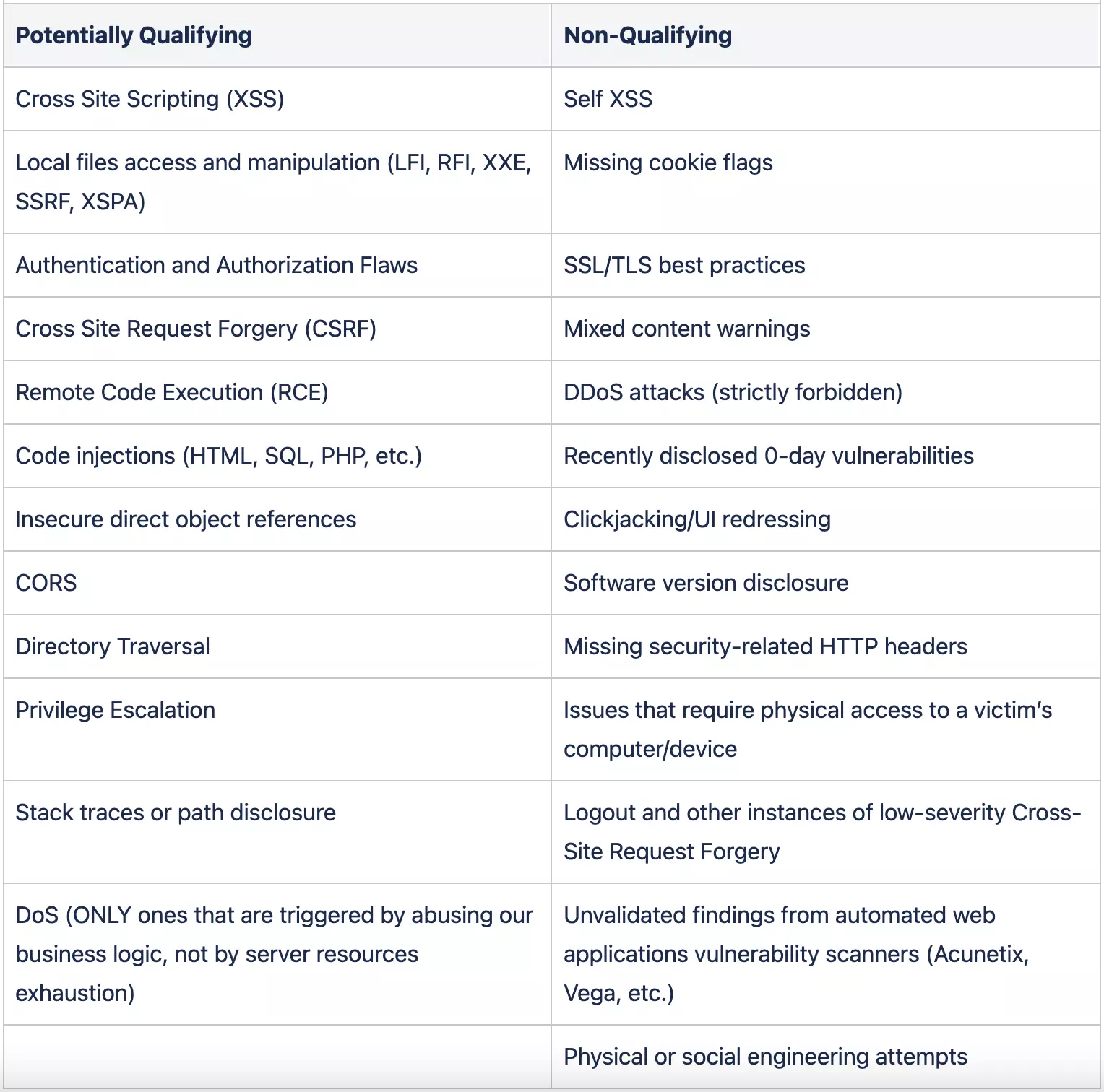
### Possible Awards In addition to mentions on our Hall of Fame and a recommendation on your profile, SMART VALOR rewards the reports based on the severity of the disclosed vulnerabilities. The following is a compensation structure for reference. **Critical** – up to 10,000 VALOR **High Severity** – up to 1,000 VALOR Kindly note that SMART VALOR has the right to determine the severity level and modify the compensation model, as well as the right to decline or reject reports that do not meet the all the requirements and guidelines described above. For the latest price of the VALOR, visit: [https://coinmarketcap.com/currencies/valor-token/](https://coinmarketcap.com/currencies/valor-token/) ### Vulnerability Examples